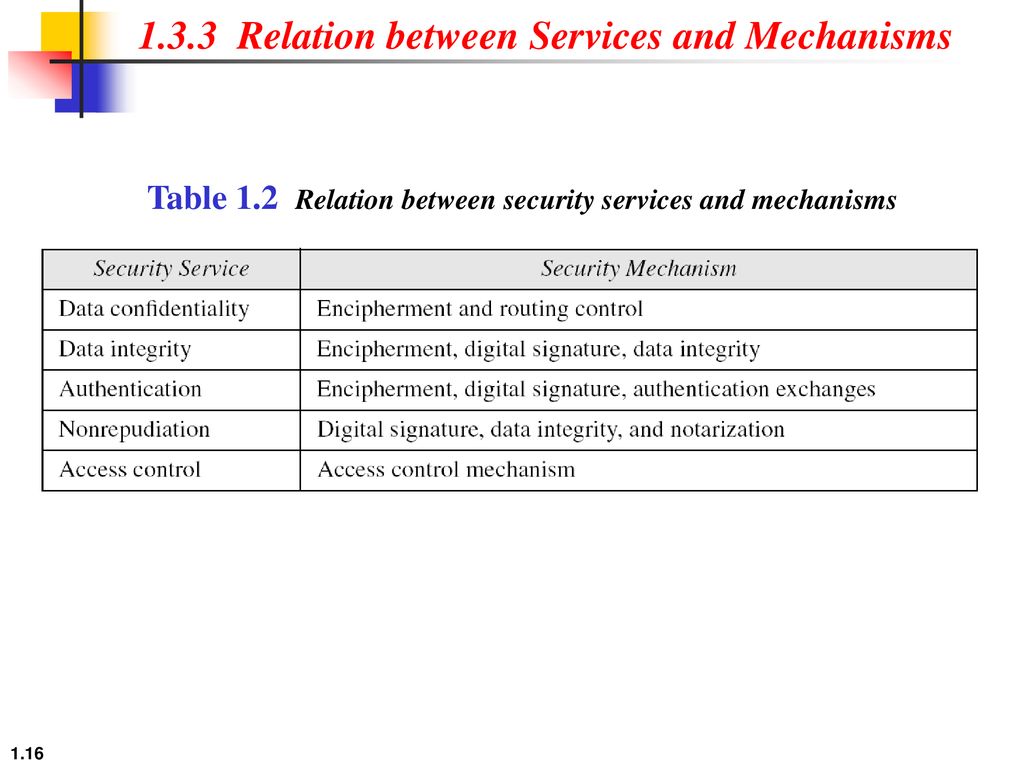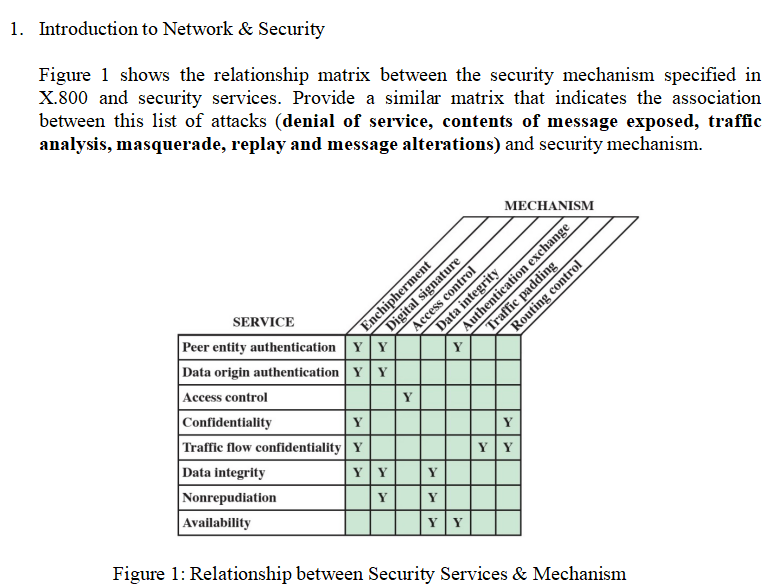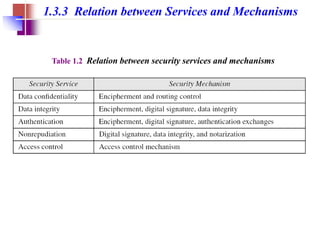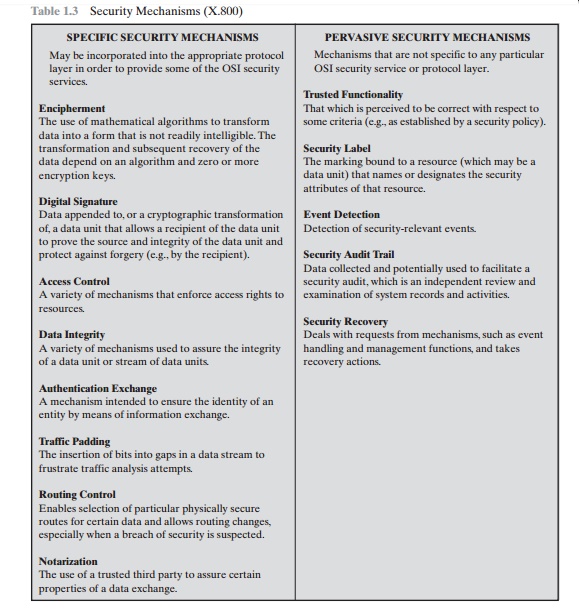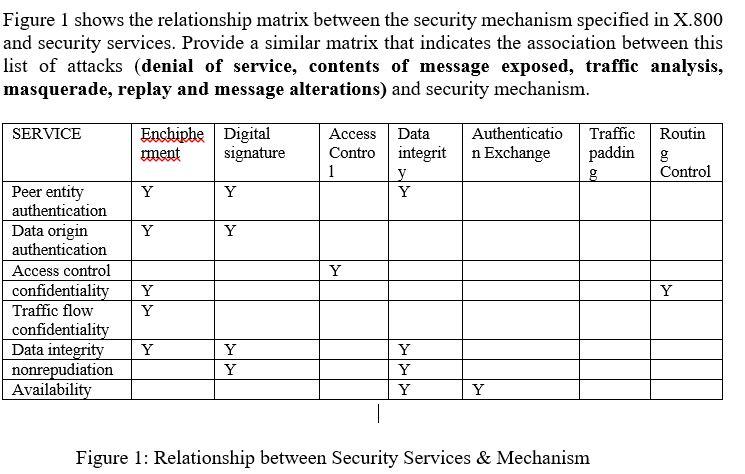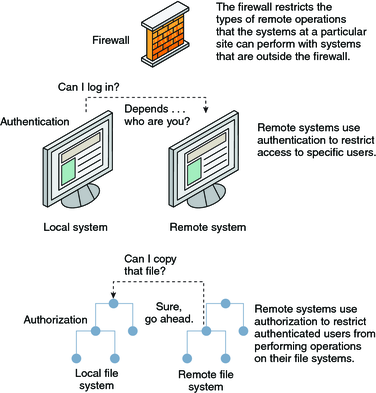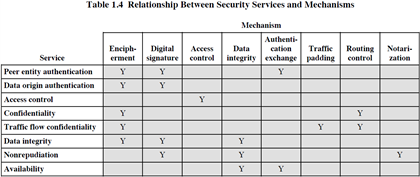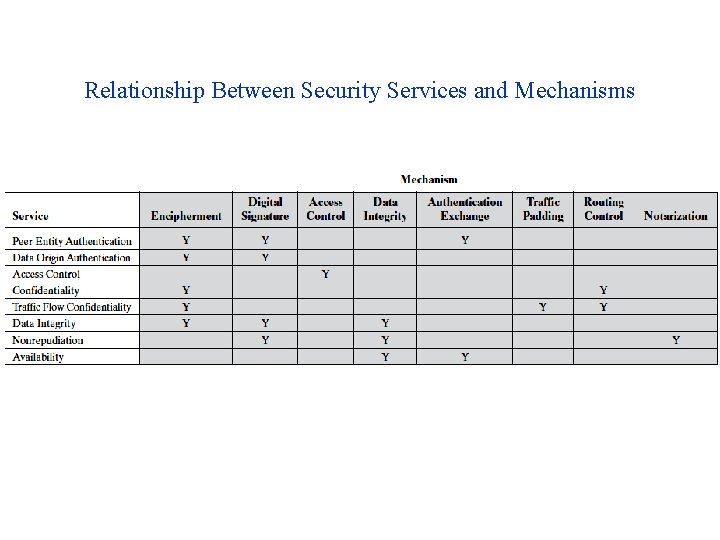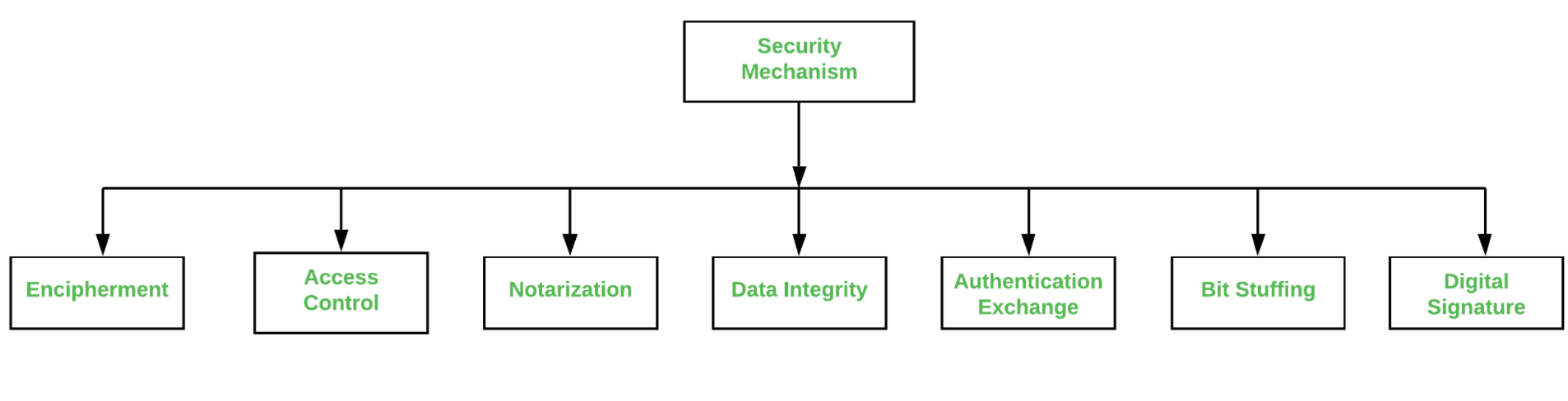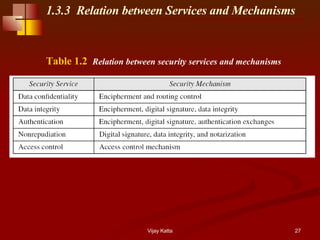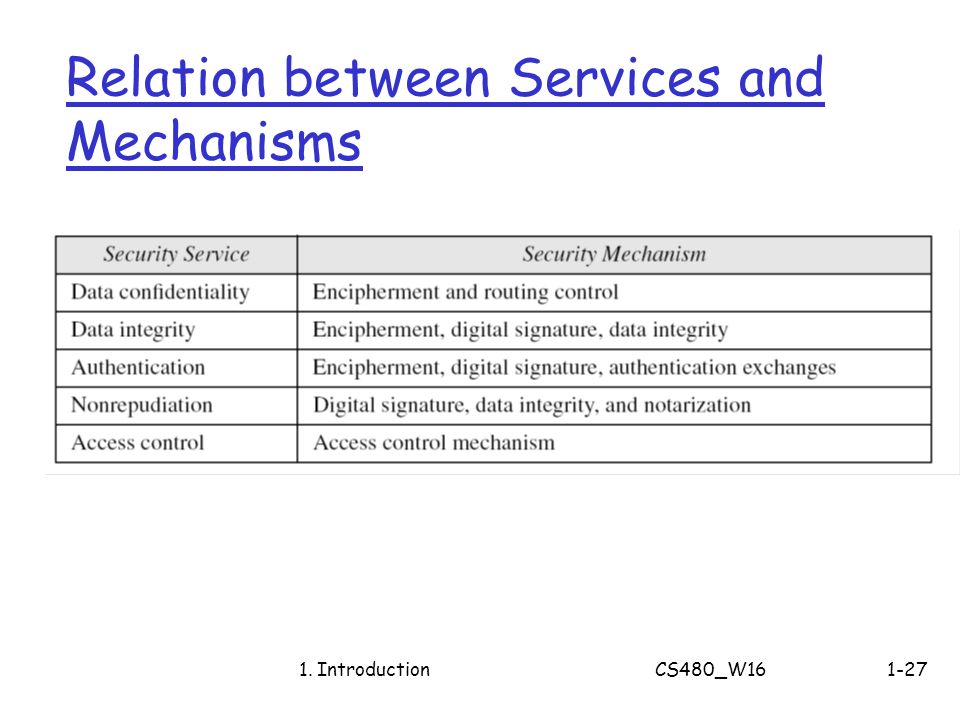
CS480 Cryptography and Information Security Huiping Guo Department of Computer Science California State University, Los Angeles Course administration. - ppt download

General Security and Privacy Mechanisms for Liberty Identity Web Services Framework | Protogenist Blog
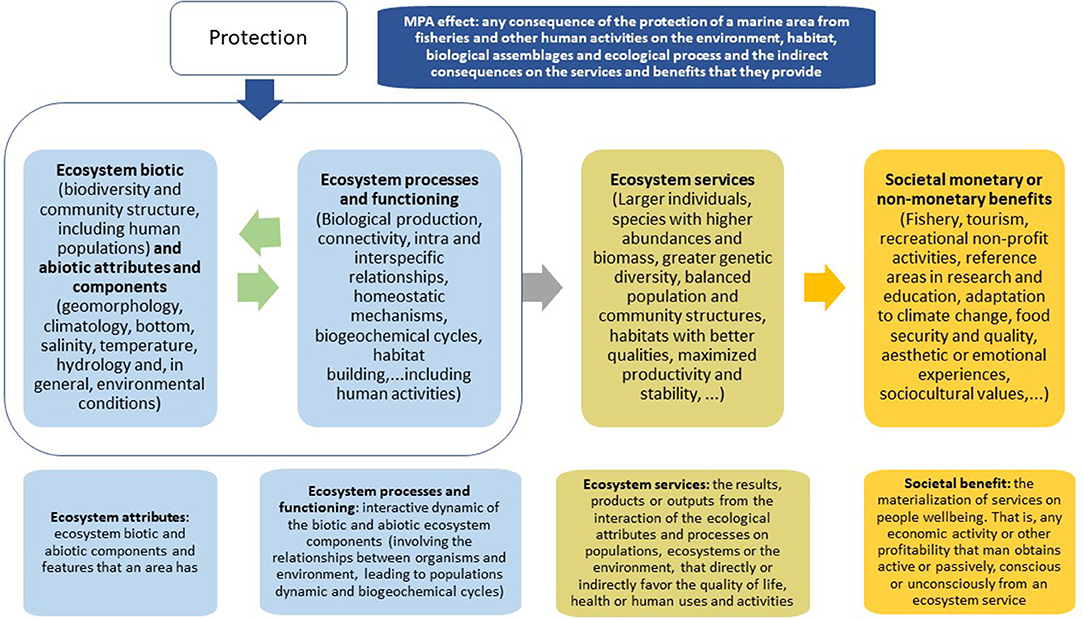
Frontiers | Reviewing the Ecosystem Services, Societal Goods, and Benefits of Marine Protected Areas | Marine Science